Abstract
What do you do when your computer won’t boot? How do you remove a file which keep reappearing? How do you recover files when your operating system has crashed?
Let the penguin show you how to scan for viruses, recover files, and fix boot problem.
What happens when you can not boot?

So you were using your computer at home last night and today, suddenly it fails to boot. What do you do now? Well the answer is reach for your rescue disk and get your system back.
We will walk you through how to bring back your computer, or at least rescue your files. Now not all system crashes or viruses can be recovered from. But often a system can be brought back with some tools and some work.
One thing we need to get straight right from the beginning is that this rescue is a Linux live CD . There are some custom rescue system which are available from vendors, but this is a general purpose rescue CD which is freely available and not tied to a specific vendor.
One more thing I should mention is that using the Rescue CD is not for the faint of heart. Most of the options are command line options which can cause damage to any system. Some of the commands could destroy a working system. Now I am not stating this to scare you but to make sure you are aware of the possible issues. With care you should have no problems addressing some issues. But when you are working on an operating system at this level it is quite possible to create worse corruption. Additionally, there is no way to anticipate every problem with a system, so the warning to back up your important files applies even more when attempting to rescue a system.
Now that you have been warned, lets get started.
I would like to say a word up front about Harakiri (Tom Kerremans) who created Trinity Rescue Kit (TRK). Much of this talk was taken directly from the online documentation which is available at Trinity Rescue Kit | CPR for your computer .
How to boot
Since this is a Live CD you need to make sure your boot config is configured to boot from it’s CD drive. Once this is setup, insert the rescue CD and wait for the boot menu. If you don’t yet have a copy of the Rescue CD you can download the ISO image here: Trinity Rescue Kit for WPCUG.
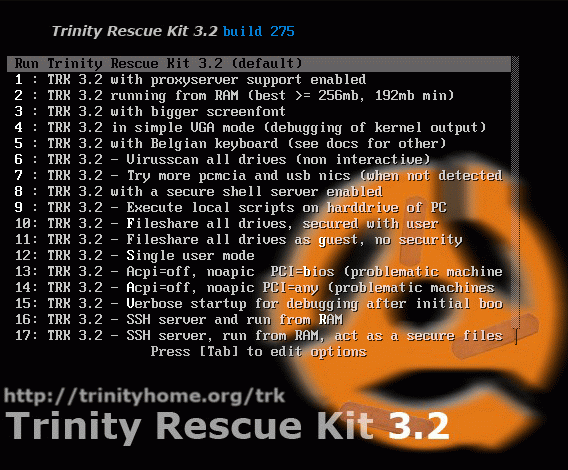
At this point you can select several boot options depending on your machine. The boot options of the latest TRK 3.2 contain a lot of different things, but most of the time the default start up will do .
Default start up This will run TRK 3.2 with all the default options enabled.
This means it will run partly from CD/usb stick, keeping your CD/usb stick unavailable for other things in the mean time, but will boot faster. Keyboard will be default qwerty and fontsize about 3/4 of a normal font in a screensize of 800x600 in VESA compatible framebuffermode. Some videocards are not so VESA compliant and can therefore not benefit from the graphical possibilities of TRK (like the Intel 815 chipset). They will have to run in textmode, preventing them from using qtparted and links (and my nice background logo)
1) TRK 3.2 with proxyserver support enabled
Start TRK with default options and prompts you for a proxyserver. In fact, it just calls for “setproxy”, which prompts you for the proxy server address (hostname or ip), portnumber and optionally username and password (leave blank for none)
2) TRK 3.2 running from RAM (best >=3D 256mb, 192mb min)
This option will run Trinity Rescue Kit completely from RAM, which means it copies all of its files into memory so your CD or usb stick becomes available for disconnection. In the case of PXE booted TRKs, you could disconnect the network at that moment. This requires at least 192Mb RAM, but recommended is 256Mb and more. Especially updated TRK versions require about 64Mb more because of the included antivirusccanners.
3) Instead of my preferred smaller 12 pixel font, use the standard 16 pixel font.
4) Run immediately in VGA mode with small fonts
If you know your machine won’t boot in framebuffer mode. As I said before: no links and no qtparted. This option is also useful in case your TRK doesn ’t initiate any output on the screen and you suspect it to hang on kernel initialization. Many times it means there’s a problem with the ACPI interface of the machine. I ’ve noticed this quite regularly on HP/Compaq machines.
5) Run with Belgian azerty keyboard.
-be: belgium
-uk: united kingdom
-dk: danmark
-it: italian
-fr: french
-pt: portugal
-nl: netherlands
-de: deutschland
-es: espana
-se: sweden
-no: norway
-us: united states
Please note that this is only a keyboard remapping, but this does not support any localised characters. This is a rescue distribution, not a desktop replacement
6) Virusscan all drives (non interactive)
This runs virusscan on all your drives. Stupid option actually, but this is about the only thing you can do that is set-and-forget without the need for any interaction. This runs virusscan without any arguments, so with ClamAV. You will get no login as long as this is running.
7) Try more pcmcia and usb nics
I found that kudzu is not really good with PCMCIA cards and USB stuff and I found out that the easiest way fix this was to just have support for pcmcia bridges compiled in my kernel, start cardmgr and try every module I find until success. Same with USB nics. This will only try this for PCMCIA and USB ethernet cards/adapters.
8) TRK 3.2 with a secure shell server enabled
Run a ssh server, a very nice feature, giving you the ability to remotely work on a machine that your nexter has started up for you.
For security reasons, you will first get prompted to create/change the password, after which in green will be displayed the IP-addresses your TRK will listen to.
9) Execute local scripts on harddrive of PC
Run local scripts from ./trk/trk3local.conf found on any local filesystem. In this way you can make computer specific scripts and put them on the harddisk. More info, see section “Triggers”
10) Fileshare all drives, secured with user
This will run a TRK with a so called Samba fileserver, which is the same as a Windows filesharing server. In this mode, you will get prompted to create a user + password that can access your server. Next, ‘mountallfs -g’ will run and share all your local drives as their respective devicename.
You can start this option afterwards from your TRK console with the command ‘fileserver -s’
11) Fileshare all drives as guest, no security
This is the same as the previous option, but this will share all your drives without any security boundary or username. Be careful with this, use only in a trusted environment.
12) Single user mode
Starts TRK in very basic mode, sometimes useful when your PC hangs or crashes on hardware detection or some other error.
13) Noacpi/noapic PCI bios - Problematic machines 1.
Some problematic machines with lousy ACPI controls might boot with this option. Happens regularly on some older Compaq machines. This will disable acpi and apic and will use the bios’ PCI routing table. Try this when TRK hangs on early startup.
14) Noacpi/noapic PCI any - Problematic machines 2.
This is almost the same option as the previous one, but I let the kernel decide what PCI mode should be used. I needed this mode on the brand new HP DC7700 machines with Intel Duo Core because it hung on kernel initialization in the PCI part.
15) Verbose startup for debugging
I use this to see what scripts are doing or sometimes your PC might hang on something but you don ’t know what: try this, but don’t get frightened by all the output.
16) SSH server and run from RAM
This is a combination of option 2 and option 8. This is a quite common combination you would need when cloning PCs from 1 TRK to another and you only have one TRK cd handy.
17) SSH server, run from RAM and run a secured fileserver
This is a combination of option 2, 8 and 10. If you want complete remote control of the TRK machine.
18) Memory tester memtest+ v1.65
Almost every distribution comes with this on startup, but this way it’s included in this one too. Nice to test your memory banks with, but real life tests are still much more certain. Still, it might do the trick for you and find you a bad module.
Linux VS Windows conventions and commands
Before we get started in how to work on your computer lets discuss some of the differences between seeing the world thru Windows glasses and Linux glasses. Although OS/X on a Mac is really a Unix based system as it Linux.
I should state up front, we are going to spend most of our time on the command line. The good side of this is that it makes our work fairly fast. The down side is that you either need to remember the command, or have a quick way of looking them up. Since this is a rescue CD, which I don’t expect you to be using often, I am providing easy help on the CD itself.
In this sub section, I am going to discuss concepts and commands which work differently in windows and Linux. The idea is not to turn you into a Linux fan, although I would be glad to have you join our Linux section. But so you understand the way things work under Linux.
For those of you who are already familiar with working on a Dos command line, much of this will be similar. BUT , there are a few critical differences. So please pay attention, I will try to teach you the commands you need, and when there is a comparable dos command I will include a comment in Italics like this.
This is not meant to be an exhaustive list of differences. If you want a more complete list have a look at: UNIX For DOS Users .
Virtual Terminals
In the bad old days, when MS DOS was the operating system of choice, we only had an ASCII terminal to type our commands into. Well, when you do not enable the X-Windows interface in Linux you get an ASCII terminal. Now this is the interface you get when you run this Rescue Kit.
Now this is Linux so although you get a text interface, you actually get 6 text windows to use. The way you access these virtual terminals is by using the key combinations ALT plus F1 - F6 . This means that you can use one virtual terminal to display help, and go to another to run commands.
One trick that is available in the virtual terminals is to be able to scroll back. If you were using a dos box in windows, you could view previous output by moving the slider up. But on a virtual terminal you don’t have a slider. BUT, in a virtual terminal you can use the key combination Shirt Pg-Up to scroll the window up.
Help in Linux
One problem in using command line systems is remembering the commands. Well for this rescue CD there are several types of help available. The first one is that the documentation from the Trinity Rescue Kit is available online. You can display it with the command lynx /usr/share/doc/helpdocs.htm . Since this system uses virtual terminals, you can read the document in one terminal, and then switch to another one to execute commands.
Another form of help on a Linux system is the Manual command. Not every command has a man page but many do. You can access this help with the command man <command> . Additionally there is a search which can be used with the man command. This is available as man -k <command> .
Another source of help for many commands is to add the help option to the command. For example if you wanted help for the command virusscan , you could type the command virusscan -h to see the help contained in the script.
Finally, I would like to point out some other sources for help. These are some additional sources of information about Linux commands External references .
Forward and Back slashes
One of the first things that drives many windows users crazy is the usage of the Slash / and the Back Slash \
In windows, the Back-Slash is used to separate directory names, as in c:\home\john . While in Linux, the Slash is used to separate directory names, as in c:/home/john .
In Windows, the Slash is used to indicate options as in dir /s . In Linux command line options begin with a dash instead, as in ls -l .
In Linux, the Back-Slash is used as a quote character. Which means that a special character looses it special meaning. For example you can change to a directory which includes a space in it’s name either as cd “Program Files” or as cd Program\ Files . Here command interpreter ignores the space as the end of a parameter.
Drive Letters VS Mounting
Another concept that is considerably different between Windows and Linux, is the concept of drive letters versus mounting.
Since I am reasonably sure that this audience knows about hard disks and partitions I will not explain these, unless you want. So in windows we talk about a prompt being C:\dos I am referring to the directory dos on the first hard disk partition. Or if I wanted to drill down further in the drive tree I might look at C:\home\john\bin as three directories deep on the first hard disk partition.
Drive letters are typically assigned by Windows, when the OS is installed. Generally the hard disk partition which contains the operating system is the C: drive. The second partition or drive is usually the D: drive.
Inside each partition the file system is a tree structure beginning with root / on each drive. Sub directories are created below the root on each drive.
In Linux we have a file system again based on the same type of tree structure, with the root at / . The biggest difference is that there is only one file tree, not one per partition. So the question is how does Linux deal with multiple partitions / disks. The answer is the mount command.
So lets see how we can use this mount command. First we need to know the names of the partitions. Once the system is running you can display this information with the command cat /proc/partitions . The output from this command on a system with one hard disk and three partitions might look like this:
/dev/hda
/dev/hda1
/dev/hda2
/dev/hda3
In Dos term the C: drive would correspond to /dev/hda1, the D: drive to /dev/hda2, and the E: drive to /dev/hda3. Now if we wanted to work on the Windows C: drive we could attach it to some point on the file system tree. Lets create a directory mkdir /mnt/C . We can now attach that partition to this directory with the command mount /dev/hda1 /mnt/C .
Typical commands
Here is a run down on the most common commands. These are how to manipulate files and folders under Linux.
List Files command in Linux is ls . This is equivalent to the Dos command dir . Typically I use the command with some options ls -axF . This command displays the current directory and shows which files are executable and which are folders. The executable files have an asterisk * at the end of it’s name. The directory names are followed by a slash / .
Change Directory is done with the cd command. This is the same command as dos cd .
Copy files is done with the cp command. This command can take multiple file names or wild card as does the dos command copy . In Dos the wild card command is *.* , but in Linux the wild card command is * .
Rename files is done in Dos with the ren . But in Linux the command is mv . One interesting use of the mv command is to move a directory tree to a new location such as mv /home/john/working/* /home/sam/working . This will move all the files under /home/john/working to the directory /home/sam/working.
Delete files is done in Dos with the del command. While in Linux the command is rm . One interesting fact is the Dos command to delete a directory is rmdir , which is the same command in Linux.
File Editing is often done in Linux with the vi command. Many casual user have trouble with this editor since it is a modal editor. You edit a file with the command vi <filename> . You move to where you want to enter text with the arrow keys and press i to change to insert mode. When yo are finished typing press ESC to exit insert mode. To save the file type :w to write the file. Then type :q to exit. If you want more information have a look at What is vi? for more information.
Virus Scanning
Virusscan is a script that actually wraps 4 different virusscanners into one. Only one of them is actually included on the TRK cd, the others are downloaded from their website upon usage.
When running virusscan, it is highly recommended that your computer has a decent Internet connection so you can get the latest virus signatures.
Clamav
Included in TRK is the GPL licensed Clamav, which is a decent scanner with very up-to-date support against the biggest virus threats and worms. I personally use it on the Trinityhome’s mail server and so far NO virus has passed since it was installed in 2004 (except when it needed to get updated since a long time). I make sure the latest clamav engine version is included in TRK.
You can manually update Clamav if you put the latest daily.cvd file on the TRK medium in <trkmedium>/trk3/clamdb
The pros of Clamav are:
very quick on new virus outbreaks
included in TRK
GPL licensed, so free for everyone
The cons:
slow and very CPU and memory intensive
detects the least viri of the 4 scanners in TRK. Because it’s in fact a mailserver scanner, it will focus more on worms than on filth that comes from malicious websites and such.
cannot disinfect inside files on its own. What I did in this case is quarantain the infected files into a tar.gz archive in <scandestination>/TRK-INFECTED/. Should a file be accidentally deleted, you can recover it afterwards and rescan it with another antivirustool
F-prot
This antivirus tool and all the others are not included in TRK but get downloaded from the Internet as soon as you call upon them. They disappear after a reboot of TRK. If you want them to be available after a reboot, you have to run updatetrk. This will be explained later in this documentation.
The pros of F-prot:
lightweight, not a big download
pretty fast, low cpu usage
good disinfection method
The cons:
does not detect everything
their website sometimes fails and download of f-prot is aborted
Grisoft AVG
My personal favorite. It’s the fastest of the bunch and detects the most viri. It even detects certain malware, adware and spyware, but it doesn’t disinfect them. For that you probably need their spyware util, which unfortunately only exists for Windows. But some get detected and this is written to a logfile. Virusscan is written in such a way that it offers to delete these files after scanning.
Pros of AVG:
detects most of all 4 antivirus tools
also detects certain malware
fast
Cons:
big download, since the virusscanners are unpacked into the ramdisk, it requires a computer with sufficient ram (at least 256Mb, more is recommended)
cpu intensive, yet the computer stays very well responsive
version and website changes often which can result in file being unavailable for download. I’ve captured some of that in a way that you first get the right url from the trinityhome site.
BitDefender Scanner
The latest addition to TRK. It has a good average between filesize, cpu/memory load and virusdetection. It can detect many different types of malware. From what I’ve experienced so far, it may detect other viri and malware than the other 3. I recommend to sweep with this after another one has already run.
Pros of BitDefender Scanner:
detects quite some viri
pretty fast
detects alternate malware
Cons:
sometimes doesn ’t detect very common viri
slow update process
Usage of virusscan
Below is the help output when you type ‘virusscan -h’. It ’s self explanatory, with an example
Usage: ‘virusscan -a {clam,avg,fprot,bde} -c -g -n -d {DESTINATION}’
-a What antivirus you want to use. Takes ‘clam’ for ClamAv, ‘fprot’ for= F-Prot, ‘avg’ for Grisoft AVG and ‘bde’ for BitDefender.
Note that ClamAv is actually meant to plug into mailservers and block infections. Therefore it can only quarantain infected files not disinfect them. BitDefender proposes disinfection as a first action and deletion as a second If the parameter ’-a’is omitted, ClamAv will be the default
-c: Use Common extensions: (only with ClamAv, speeds up scan a little)
-g: Get only, just download the AV and updates, no scanning. For use with updatetrk
-d: Destination folder to scan. If no destination is given, virusscan will scan all local filesystems it can find. You can specify multiple destinations when you separate them with commas (wihthout spaces behind)
-n: No update. Don’t check for new AV signatures
-h: Displays this helpmessage
Example: virusscan -a avg -d /mnt0,/hda1/WINDOWS,/hda1/Program\ Files This downloads and updates AVG if not available and scans the locations /mnt0, /hda1/WINDOWS and /hda1/Program\ Files
Winpass and regedit
winpass By default it will reset the builtin administrator account of a locally installed Windows, but you can specify other accounts as well at the commandline. In fact, you can add any parameter from chntpw which will be parsed to the commandline. So winpass will list you all usernames found in the SAM. Should you have troubles that metacharacters are present in the username (like the Ø or something), you can still use the HEX reference to the username listed next to it. Be sure to prepend that with a ‘0x’. More info on that can be found in the manual of chntpw. Watch out with disabling syskey! Most of the time you don ’t need to disable syskey. It removes strong password encryption, so all local passwords become invalid, since the hashes don ’t correspond to the encryption algorythm anymore. This has been known to cause problems with Windows XP’s product activation. Read the warning well!!!
regedit
Regedit this is actually the same script as winpass, but called in this way it copies all registry hives and opens them (sam, security, system and software). Only drawback is that it cannot know which user registry to open, since they are located in different directories. Because chntpw is not scriptable, I cannot read registry hives from a shell script to determine= the location of userhives.
Once running, refer to the documentation of chntpw/regedit on how to use it.
After you did your work in the registry, just exit and the changed hives will be written back.
File Rescue
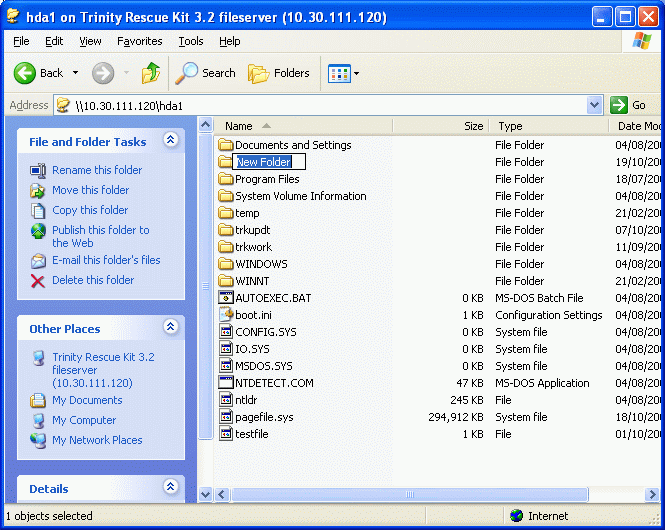
The problem with recovering files from a crashed server is being able to get at the files. On a Linux server you can share files with a windows box by mounting the files as part of a Samba fileserver.
The command Fileserver allows you to share your drives like a windows fileserver The “fileserver” util actually runs a samba fileserver on your TRK.
It read-write mounts all your local drives by calling ‘mountallfs -g’ and then shares all your found partitions as their device name. So if /dev/hda1 was a ntfs formatted partition on host 10.0.0.1, it would be shared as \\10.0.0.1\hda1
Fileserver can be called in two modes: in secured or in guest mode.
Secured mode is invoked with the command ‘fileserver -s’ This will prompt your for adding a user and a password that will have access to your files remotely. Just follow instructions. Here’s how the output would be if you ran it.
Starting a username/password secured Samba fileserver and sharing all local filesystems
Enter a username which will be created to have access to your local files:
New SMB password:
Retype new SMB password:
Added user testuser.
Mounting all your local filesystems using mountallfs -g
These are the IP-addresses your fileserver will listen to:
192.168.81.5
Starting SMB services: [ OK ]
Starting NMB services: [ OK ]
Guest mode is invoked with the command ‘fileserver -g’
Use with caution, it allows everyone with network access to the computer to go on the local harddiscs. Use only in a trusted environment with a firewall or not connected to the Internet.
Bootsector repair
Several utilities can be applied to repair a bootsector and there’s a lot to be said about it. I ’m only describing a few procedures for Windows and Linux bootsectors.
In a PC style (x86) environment there are 2 ways a machine can boot from a harddisk: or from the MBR (Master Boot Record) OR from the bootsector on the active partition. Historically, Windows has always booted from the active partition bootsector, but it also writes some stuff to the MBR of the disk. I don ’t know all the internals of the different bootprocesses, so please correct me if this documentation has it wrong.
Continuing: Linux can boot in the two different ways: or it writes its code to the MBR (e.g. /dev/hda), or it writes it to the active partition (e.g. /dev/hda1).
Check partitioning
Sometimes the failure to boot can simply be a partitioning problem. In t= hat case, refer to the previous section. If you rebuild your partitionin= g like it was before, it is most likely to boot again. Never forget to set the right active partition!
Windows boot
Let ’s take a quick look on procedures how to repair Windows bootrecords. As I already said Windows booting depends on both MBR as partition bootrecord code.
ms-sys
This utility can write new MBR code to your disk. Type ‘ms-sys -h’ to get some help on the different parameters, but in most cases you run it first to analyse your disk ‘ms-sys /dev/hda’, which will tell you how your MBR.
‘ms-sys -m /dev/hda’ will write an XP style MBR to your disk.
Remember that this utility handles only about the MBR. For the windows bootsectors you must refer to other utils.
testdisk
I’ve tried testdisk to write new MBR code and it worked like a charm for me. What ’s also nice about it is when you go into advanced mode, you can analyse also the bootsector of the partitions and repair them if needed.
the Windows bootcd way
It might happen that none of these methods get you back into booting Windows, then there is one last method that you can try, which actually has nothing to do with TRK: boot from the Windows XP cd and go to the recovery console. Make sure you know the password of the Windows system on the local disk. Otherwise, reset it first with ‘winpass’ on TRK.
Now, booted into the recovery console, it ’s a good thing to run checkdisk first: ‘chkdsk c: /p’
Next run ‘fixboot’
And finally run ‘fixmbr’
‘exit’ to reboot
Recovering lost partitions
It can happen you did something stupid or something inexplainable happened and your partition table is gone or corrupted.
To recover your partition tables, there are a few methods.
Fdisk
I’m not talking about the Microsoft dos version of fdisk, but of fdisk on Linux.
Actually what you do with this is manually redesign your partition table. Of course, the risk here is that you have absolutely no idea of what your partition table was before if you had more than one partition. So this is good in case of a disk with a single partition.
And let’s say in this case that partition contains an NTFS filesystem on /dev/hda1
Make sure nothing is mounted (run umountallfs)
Run fdisk:
‘fdisk /dev/hda’
In fdisk: ‘p’ to print your actual partition table
If your actual partition table is a bad one, erase by removing each partition with ‘d’ and answer with the right partition number (in case of logical drives, first remove everything equal and above 5).
‘n’ for new partition
Choose primary partition, press enter for start and end sector. Fdisk automatically assigns it as a Linux native partition.
‘t’ to toggle the partition type. Ntfs is ‘7’
‘a’ to make it active (choose ‘1’), since it ’s probably the bootpartition
‘w’ to write your changes
If this was your previous partition layout, you should now already be able to mount the ntfs partition. If not, you probably won ’t be able to boot from it either. But it should be, since this is the way to do it when the problem was simply a lost partition table.
Testdisk
This is the more advanced method of recovering partitions. Run ‘testdisk’ at the commandline, the rest speaks a little for itself (Intel partition table Analyze etc.). Read the testdisk documentation at cgsecurity.
Testdisk is also very nice to repair bootsectors. Just play with it a little on a testmachine to see what it all does. I’ve played around with it myself, and although there’s no guarantee that you will be able to repair the bootsector all the time, it still did a pretty good job where others failed.
Another thing I can recommend you about testdisk: if it doesn ’t find all of your partitions in the first minute, there ’s probably not much left but some free disk space without a valid filesystem. It’s safe to cancel already if you think it found all you need.
Cfdisk
A menubased fdisk replacement, easier to use than standard fdisk
Written by John F. Moore
Last Revised: Tue 01 Sep 2020 08:10:09 PM EDT

This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 3.0 Unported License.
